The pandemic this year forced admins to scramble to keep their Windows systems up and running (and properly patched) at a distance. So it's important to understand what options are available and which work best in different situations.
If you asked a normal user what they dislike most about Windows 10, the answer would likely be related to patching, rebooting and the generally confusing update process. Entire web sites have sections devoted to explaining the updating process and how to manage it — and I’ve written my fair share about the topic.
In addition to writing about Microsoft patches here (and about Windows security for CSO), I’m also a moderator on the Patchmanagement.org listserve. We have many people who rely on various patching tools to deploy updates and maintain workstations. There are a number of options, so it’s important to understand how they work (and how they vary) so you can get the most out of them.
Microsoft itself has several: There is, first, the basic Windows update most consumers and home users use. It allows each workstation to independently reach out to Microsoft’s update servers for needed patches. The advantage? It’s built in, costs nothing (other than bandwidth), and is set up from the get go. The disadvantage? It’s doesn’t give you much control over when and how updates download — and how it behaves has changed over the years.
Microsoft also has a network-based patching platform. I’m old enough to remember when it was called Software Update Services (or SUS). Originally, it involved a separate download; now it’s a part of Windows Server. But over the years Microsoft has been pushing away from a domain based/on-premises software delivery system and moving instead toward alternative patching platforms such as Intune (now of Microsoft 365) and Windows Update for Business. That latter one sounds like a standalone platform; in reality it’s a group of group policies or registry keys that allow you to set rules for when Windows will install updates.
The advantage for Intune is for those who have fully embraced the Microsoft 365 subscription model. Workstations can be managed and controlled by an online console. Windows Update for Business is a hybrid compromise: it gives an admin enough group policy controls to let workstations apply updates but little insight into completion and issues.
And let’s not forget Windows update delivery optimization, which builds on the standalone Windows update concept but allows workstations to grab bits of update code from fellow workstations. So if workstation A downloads bit 1, and workstation B downloads bit 2, they share that code between them without having to go back to Microsoft and downloading the same bit twice. Early on it was buggy, very buggy, and I disabled it on my home network because it saturated my bandwidth. It’s much better behaved now, but it still doesn’t have a console for reporting.
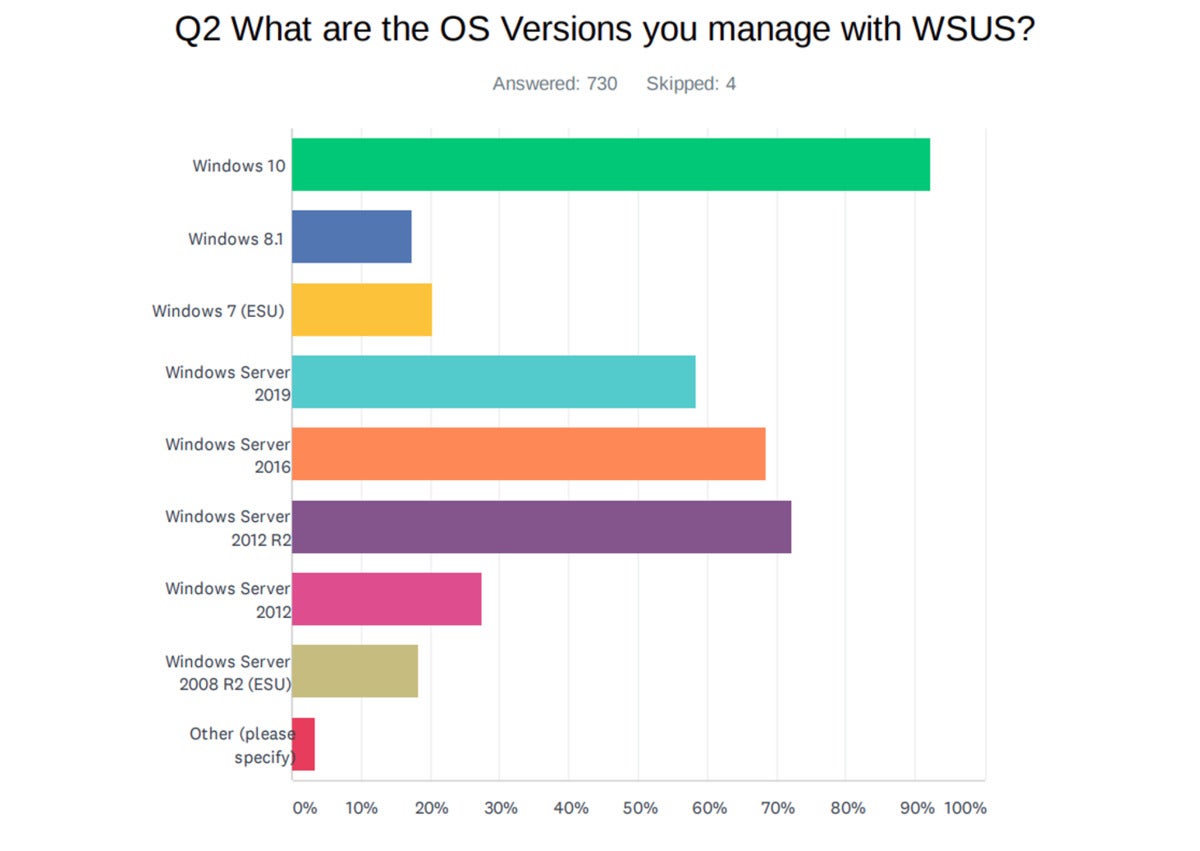
As part of my work with Patchmanagement.org, I asked IT admins earlier this year about Windows Server Update Services (WSUS). My goal was to get a feel for what they thought about the patching role for on-premises servers and to see if they were happy with WSUS in its current condition. Some IT professionals feel that Microsoft has not been adding needed resources, instead focusing on newer patching options such as Intune. (One third-party developer, AJTEK, not only provides information on how best to set up WSUS, but also offers additional scripting and maintenance scripts to better maintain WSUS.)
The reason I wanted to do the survey was to get a feel for those that use Microsoft’s original network patching tool and if they see, as I do, that Microsoft seems to be focusing on Windows Update for Business and Intune going forward.
I think there needs to be something that provides a single-pane patching view for administrators that isn’t as tied to Intune. With all the changes thrown at IT during the COVID-19 pandemic this year, we are moving faster to cloud deployments — but we aren’t fully there yet. Seeing so many WSUS administrators say that services still serves a need, especially for firms that are budget conscious, tells me people will stay with what works for now, even if it could work better. That’s especially true with the economy still in a precarious state, (as is IT spending).
The pandemic — with its shift to remote work and getting employees on any laptop they could find – has shifted the patching landscape this year. During the early days, IT admins had to pivot from patching and controlling updates centrally through WSUS to patching machines over a VPN. (Thankfully, Microsoft early on issued guidance on how to set up a split-tunnel VPN to allow workstations to pull updates directly from home internet rather than from across the VPN connection.) Other administrators are looking for options to not only control Windows updates but third-party patching, as well.
Some admins use tools such as Chocolatey, which can be used to deploy and maintain Windows 10 apps. (The paid version of the platform, Chocolatey for business, is more geared toward business deployments.) Another platform I’ve seen used for patching and maintaining applications, including third-party programs, is Ninite — in particular Ninite pro. In addition to Windows patching, it can also provide patching to other applications on your network.
It’s clear that this year has forced us to rethink how we set up and maintain our Windows ecosystems. We no longer have workstations tethered to one domain behind one firewall patched by one mechanism. Going forward it’s unclear whether Microsoft will provide any new features or reports to its venerable WSUS patching platform. But users do want improvements. It’s also unclear whether Microsoft plans to invest in those kinds of improvements or instead sees a workforce that is more mobile, more work from home, more work from anywhere. If it’s the latter, admins could be forced to look for new and different tools to patch and maintain our networks.